PGP | What is it and how to use it?

PGP stands for ‘Pretty Good Privacy’ but it is much more than that. It is the open source gold standard mechanism for encrypting/signing email, files and other data. It can be a challenge to understand in the beginning, so I am here to give a crash course into PGP and how it works.
Admittedly, PGP is not the most widely used or user friendly means to encrypt files and email. It can be a bit difficult to understand at first and may even seem cumbersome to use. While that may be somewhat true, it is the most secure way to ensure confidentiality and integrity of data both at rest and in transit.
I will start by explaining a bit of what PGP is and how it works. PGP encryption was created in 1991 by Phillip Zimmerman. It is ‘Asymmetric Encryption’, which means there is a private key (always kept secret) and a public key (available to anyone).
For this type of encryption to work, someone wanting to encrypt data and send it to someone will use the recipients public key to encrypt the data. Once encrypted, the data is sent to the recipient, who uses their private key to decrypt the data. This provides data confidentiality as the data is ‘encrypted in transit’. If it is intercepted a bad actor somewhere along the communication path, it will be unusable.
Sending encrypted email
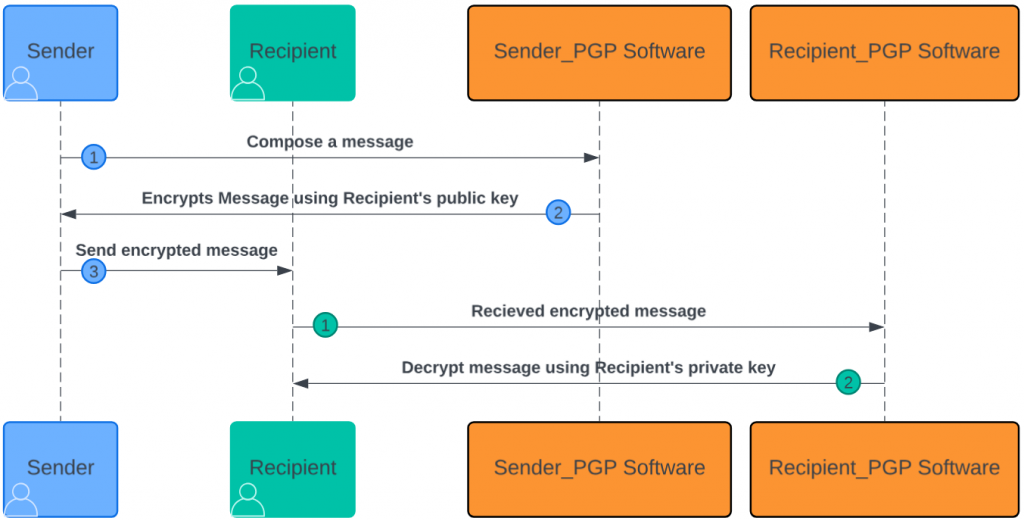
In looking at the diagram above, you can see how process of sending and encrypted email using PGP works. In this case, the ‘PGP Software’ on the sender and recipient side is just the email application that the user is using. In some cases, this is provided through an additional ‘plugin’ that must be installed in the email client. In other cases, PGP is supported natively. One email client is that supports PGP natively is Thudnerbird, which is a well known open source email client developed by Mozilla.
Sending signed email
In addition to being able to send encrypted email, PGP can also be used to ‘hash’ and ‘sign’ email. Essentially, this is a means to ensure that the sender is who they say they are and that the email has not been tampered with in transit. In this scenario, the email is not encrypted, so it can be read by anyone that intercepts it. This provides data integrity and non-repudiation by comparing a one way hash of the data created by the sender and validated by the recipient.
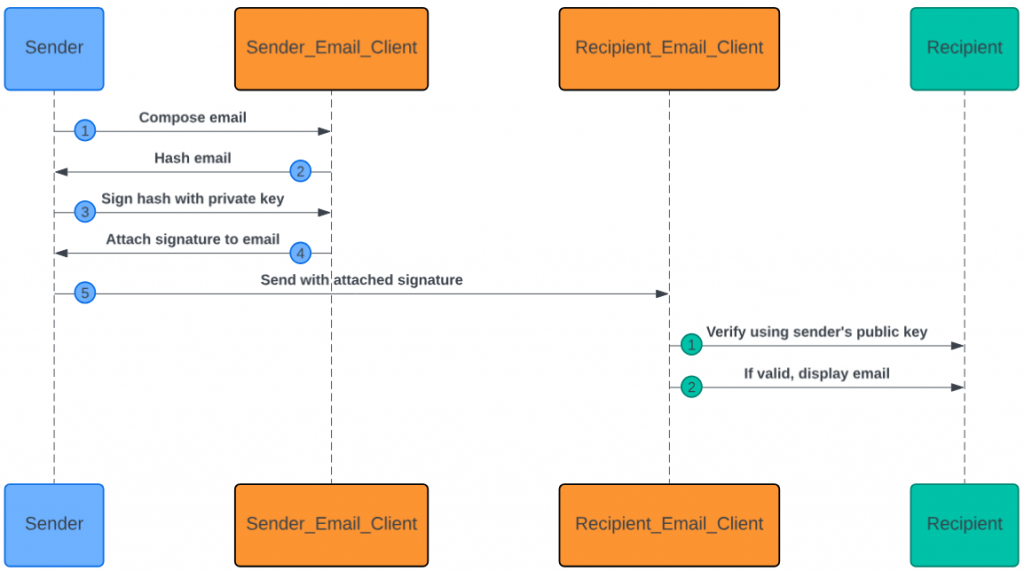
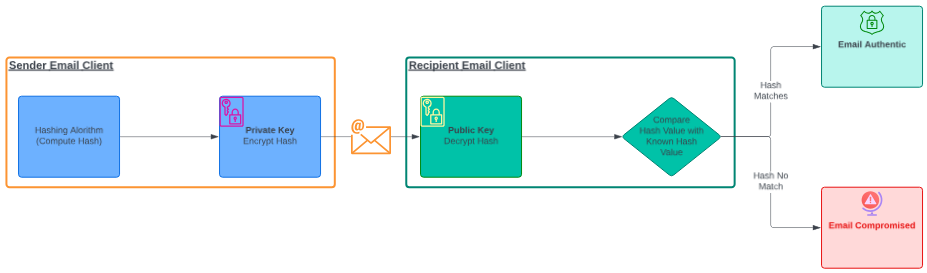
The process of ‘signing’ an email requires that the email first be ‘hashed’. Hashing is running data (an email in this case) through a hashing algorithm. This algorithm generates a random string of characters that represent the files content – called a ‘hash’. The hash is encrypted and attached to the email. The encrypted hash can be decrypted with the senders public key. When the recipient receives the email, they can re-hash the email on their side and compare the result to the value of the known hash (the one attached). If the file content changes, the hash of the email also changes and the email cannot be authenticated as the hashes do not match. In this case, the email should not be trusted.
Key Management
Key management is a fairly broad subject. It is also sometimes subjective. People decide how best to manage their own keys, which takes some thought. Below, I will try to answer some common questions to address encryption keys in more general terms.
What are ‘encryption keys’ and how do you get them?
Encryption keys come in many forms, with many algorithms and bit lengths (..and more..) but lets focus on PGP for now. With PGP, you generate your own keys, using a PGP key generator. Depending on the operating system that you are running, you may need to install special software. A good one for windows is gpg4win (that is not misspelled). GPG is ‘Gnu Privacy Guard’ and is basically interchangeable with PGP.
How do you share your public key efficiently with others so you are able to exchange encrypted email?
Most PGP utilities allow you to ‘publish’ your public key on public key servers. This makes your public key available to anyone that wants to find it. Email clients with PGP support, such as Thunderbird, also allow publishing and will look up recipients that you email to see if they have a published PGP key. Alternatively (clandestinely?) you can share public keys directly with someone on a USB drive. When you do this, only you and that individual can exchange encrypted emails (unless someone leaks a key to others).
What happens if I lose my private key?
The short answer is – you are screwed. At least as it relates to anything that has been encrypted using that key pair. Both keys are required to encrypt/decrypt data. If one is lost, there is a potential that anything encrypted with that key pair could also be lost. The good news is, you can revoke a public key that has been published (and lost), generate a new key pair and start over. Moral of the story – Remember to backup your keys!
Summary
PGP is a very strong, reliable and efficient means of encrypting and exchanging sensitive data. It is a bit cumbersome and takes a bit of getting used to, but it is highly secure, has a long record of success and is used by millions. It has applications outside of email as well. You can encrypt files in much the same way and store them securely. Encrypt backups for secure storage. Sign files to ensure integrity. The list goes on.
If you have a need to encrypt data or communications and want something well known, trusted and free – PGP is the way to go.